After spending over a year in the Swiss Armed Forces as part of my mandatory military service, I’ve had some motivation to learn more about cyber warfare and how it’s being actively used. But not just how it’s being used at the moment, also what happened in the past that could have changed the world in one way or the other.
This is a non-technical and small post - I will write more technical posts soon…
What is “Cyber Warfare”?
“Cyber Warfare is the use of the internet to attack an enemy, by damaging things such as communication and transport systems or water and electricity supplies.” 1
The definition is pretty straightforward and there’s nothing big to add to it. However, just having such a definition may mislead people into thinking that it’s “just” on the internet and damages are most likely “just” on the computers themselves, and not some infrastructure.
The impact cyber warfare has may be far more important and damaging than what most people think.
If you are interested in the hacking tools of the CIA - the Vault 7 Leak is very interesting in seeing the capabilities the agency has.
Why is it a silent battlefield?
Unlike conventional warfare, cyber warfare is not being waged with bullets and bombs but with code and covert operations.
If you do not have systems in place to detect anomalies or malwares on your network, you will not see anything. However, Stuxnet showed that even if you have monitoring capabilities, a malware may fake the data it shows and for any operator it will look completely normal. This exact silence and potential invisibility is what makes cyber warfare so dangerous. The damage it does can range from stolen data to destroyed infrastructures, though once it’s realized it will be too late and the harm has already been done (or at least the significant part).
Key examples
Over the years there has been some perfect examples of how cyber warfare can or could be used to defeat an enemy state, or disrupt some behavior that is not appreciated.
Stuxnet
Stuxnet is probably the most well-known example of a cyber weapon. In 2010, one of the most sophisticated worm targeted Iran’s Natanz nuclear facility - more specifically its uranium enrichment centrifuges.
It effectively caused physical harm to the centrifuges and had to be replaced with new ones; it manipulated their rotation speeds; and it did that while showing normal data to the dashboards and monitoring systems of the nuclear facility - so nobody has been aware of it, even though centrifuges getting randomly destroyed may seem very weird and suspicious.
It used 4 zero day attacks, which is quite insane - for the reference, a zero day reported in a bug bounty program may give you a bounty of thousands to millions of dollars - obviously it depends on the impact and the system targeted. As shown later, it was an attack orchestrated by the USA and Israel, under the name of Operation Olympic Games.
The name came from two keywords that are in the malware: .stub & mrxnet.sys
I highly recommend watching the documentary Zero Days, which is a perfect documentary about the Stuxnet malware.
CrowdStrike
The worldwide outage of July 2024 was not the cause of a cyber weapon like Stuxnet, however the damages and harm it caused across the globe was so significant, that it shows what could happen in a real scenario.
CrowdStrike distributed a bugged update to its Falcon Sensor software, which ultimately lead to Windows computers getting a Blue Screen of Death. The impact it had ranged from airports to hospitals to private companies.
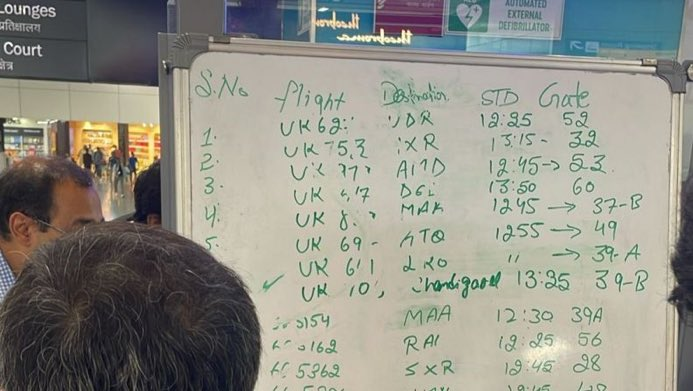
The picture above shows what the impact for an airport was. Though as you may guess, it didn’t just affect the monitors showing the departures and arrivals. Boarding passes were also filled and written by hand…
When it happened I was surprised by how CrowdStrike wasn’t able to find that bug before distributing it to millions of devices… I was also surprised how much Windows is used in the wild; and not for example a Raspberry Pi or similar - especially for displaying departures and arrivals in airports.
Now yes, not knowing the gate of your plane is not dramatic. But, for example, in hospitals they had limited to no access to patient records, and depending on patients it can be very dangerous, take allergies for example. It also affected devices that monitor vital signs of patients…
SolarWinds
In 2020, a state-sponsored Russian group, infiltrated multiple US government agencies, for example the Pentagon, the CISA, the NSA, the FAA, Microsoft, Nvidia and much more.
They compromised the update process of SolarWinds Orion - which lead to lots of organizations installing it and having a backdoor which the group was able to use to spy and exfiltrate data. The stolen data was for example the source code of products, emails, accounts and court documents.
Goals
Espionage
SolarWinds is the perfect example of espionage. Stealing sensitive data from enemies to use them in your favor.
But this doesn’t necessarily mean just stealing data. Infiltrating and staying on a network of a government agency for days, weeks, months or even years can be undetected and the attackers will gain the information it needs.
For the reference, the SolarWinds attack was undetected for months, so the amount of data that has/could’ve been stolen is very likely to be huge. And looking back at it, it could be possible that the network of an agency is infiltrated at the moment of you reading this…
Disruption
Targeting infrastructure can put a country to its knees depending on the infrastructure that is being targeted which can lead to chaos in the whole country.
Let’s say the whole electric grid of your country is just offline. What will happen to all the people that are in hospitals using machines to keep them alive? How can you contact your family members during a catastrophe. You’ll be back to living just like people used to live years ago. Now you may say - “But I can survive with no electricity” - yes you could, but for how long and in what conditions will you be living? Countries are dependent on electricity for lots of things.
Disinformation
Spreading false information online can lead to a loss of trust and most commonly lead to the manipulation of people.
I don’t need to explain how many times people have been manipulated by the media and social networks about lots of things. It will put a vision of something in your head. However, how medias manipulate people is another topic…
Destruction
Stuxnet… It destroyed centrifuges in an air-gapped2 nuclear facility. The centrifuges got obviously replaced, but what if the damages would’ve been more important or non recoverable?
What impact can it have?
A cyber weapon attacking public services such as hospitals, transportation or communication systems can have devastating consequences. Life-saving surgeries, the paralysis of entires cities and communication systems are just the most obvious examples.
Government and military organizations can also get attacked. State secrets, military plans and classified documents are amongst the most valuable data that an enemy state can hope to steal. Considering we are getting in a more and more digital world, all these documents are at the perfect location for cyber weapons: the digital world.
My opinion // Conclusion and summary
While this whole post is mostly my opinion, there are facts that cannot be ignored. One of them is that cyber warfare is evolving day after day, and very quickly. Another one is that it will never stop, quite the opposite actually, it will get more and more used.
The consequences of full-scale/massive cyber warfare has thankfully never been lived so far, and I do hope it will never be the case, as the consequences may be massive for the affected parties.
Obviously the data of a small development organization in your city is not as important as the data of the NSA to the eyes of a hacker. I still do believe that more attention needs to be given to the security of various assets.
Footnotes
-
https://dictionary.cambridge.org/dictionary/english/cyberwarfare ↩
-
An air-gap is a security measure that isolates a network by preventing it from establishing external connections, e.g. the public internet. ↩
